The simple, direct answer is that you can stop mobile apps from spying on you by implementing a multi-layered defense focused on three core pillars: Informed Consent, Granular Permission Reduction, and External Shields.
This involves aggressively disabling global tracking permissions on iOS via App Tracking Transparency (ATT), deleting your advertising ID on Android, and employing advanced techniques like setting up a Private DNS to block hidden network trackers.
While no single step can guarantee 100% anonymity, combining these methods across both the OS and network layers will significantly disrupt the two-tiered tracking system.
This tracking system relies on resettable Advertising IDs (Tier 1) and hard-to-change Device Fingerprinting (Tier 2), which apps and their hidden third-party SDKs use to build a permanent profile of your activity.
If you’ve been following the tech world, you know that the word “spy” has essentially replaced “track” when talking about mobile apps. And for good reason. It’s not just about targeted ads anymore; it’s about a comprehensive, persistent profile of your life being built in the background.
Based on my years of professional experience reviewing smartphones and rigorously testing privacy features, I can tell you that the default settings on both iPhone and Android are inadequate protection against the advanced, often hidden, methods trackers employ.
To achieve real privacy, we need to go much deeper than just hitting “Don’t Allow.”
Understanding the Two-Tiered Mobile Tracking System
Before we get into the step-by-step fixes, it’s crucial to understand the enemy. Tracking on your phone operates through a sophisticated, two-tiered system that works to identify and follow you across different apps and websites, even when you try to opt-out.
Tier 1: The Resettable Advertising ID (The Easy Part)
This is the most common and easiest-to-understand form of tracking.
- iOS: This is the Identifier for Advertisers (IDFA).
- Android: This is the Google Advertising ID (GAID).
These are unique, user-resettable identifiers assigned to your device by Apple or Google. Advertisers and ad-tech companies use this ID to link your activity across various apps and build a profile for personalization.
The good news? Both Apple and Google have provided tools (like Apple’s ATT) that make this ID less effective or easier to delete. However, many apps simply ignore your opt-out and try to use other methods, which brings us to the greater threat.
Tier 2: Permissionless Device Fingerprinting (The Persistent Threat)
This is the advanced, “un-censorable” method of tracking that works without needing to access the resettable Advertising ID or even asking for explicit OS permissions.
This is where the real spying happens, often hidden within third-party SDKs (Software Development Kits) that apps use for non-ad functions like analytics, crash reporting, or social media sharing.
Device Fingerprinting aggregates several stable, hard-to-change system properties to create a signature that is unique to your specific device, regardless of whether you reset your IDFA or GAID.
| Attribute Collected | Why It’s Unique |
| GPU Render Details | Minor differences in how your specific GPU and driver version render graphics (like WebGL) create a unique output. |
| Device Clock Skew | Tiny, measurable drifts in the device’s internal clock relative to a central server’s time create an identifying signature. |
| Localized Settings/Locale | The combination of your preferred language, time zone, currency format, and keyboard layout provides a highly distinguishing data point. |
| Installed Fonts | The unique list of fonts available on your device’s operating system, which differs subtly even between devices of the same model. |
Because these attributes are required for your phone to function, the operating system doesn’t require a specific “permission” to access them.
This makes it incredibly effective and difficult to block, meaning a comprehensive defense is necessary. The overall strategy we will pursue is a combination of Informed Consent, Granular Permission Reduction, and External Shields.
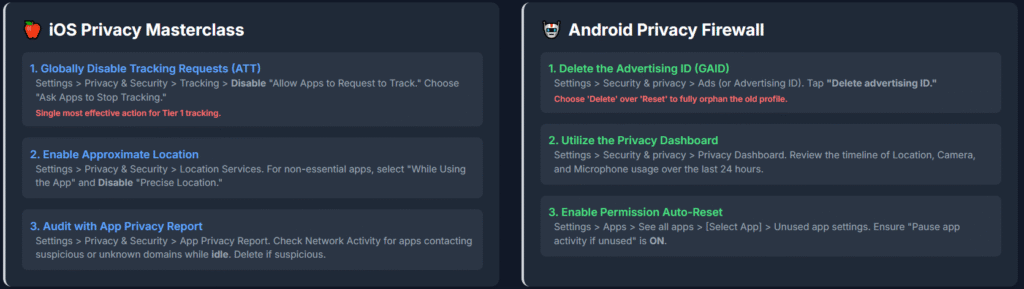
The iOS Privacy Masterclass (Apple Tracking Transparency)
Apple’s App Tracking Transparency (ATT) is a huge step forward for privacy, but many users don’t maximize its potential.
The key to stopping spying on an iPhone is to disable the tracking mechanism at the global level and then to audit what little tracking remains.
How to Globally Disable App Tracking Requests on iPhone
If you want to completely stop apps from even asking to track you across other companies’ apps and websites for advertising purposes, you must disable the master switch.
By turning off the global toggle, every app that attempts to request tracking access will be automatically treated as if you selected “Ask App Not to Track,” permanently denying them access to your IDFA(Identifier for Advertisers).
Step-by-Step Guide: Disabling Global Tracking
- Open the Settings app on your iPhone.
- Scroll down and tap Privacy & Security.
- Tap Tracking (it’s usually near the top).
- You will see a toggle for “Allow Apps to Request to Track.”
- Disable this toggle. You will be prompted with a window offering three choices. Select “Ask Apps to Stop Tracking.”
Pro Tip: In my opinion, this step alone is the single most effective action an iPhone user can take to shut down Tier 1 advertising tracking.
Granular Permission Reduction: Location and Microphone Access
Apps often request overly broad permissions (like “Always” for location) when they only need access temporarily. The most critical permissions to manage are Location, Microphone, and Camera.
The Approximate Location Advantage
Since iOS 14, Apple has allowed you to provide an Approximate Location (an area of about 10 square miles) rather than your Precise Location.
This is a crucial step in reducing the risk of location-based deanonymization.
Step-by-Step Guide: Enabling Approximate Location
- Go to Settings > Privacy & Security > Location Services.
- Review the list of apps. For any app that doesn’t absolutely need your exact street address (e.g., a weather app or a news app), tap on the app.
- Select “While Using the App” instead of “Always.”
- Crucially, disable the “Precise Location” toggle at the bottom of the screen.
Pro Tip: While testing, I discovered that most apps function perfectly fine with “While Using the App” and Approximate Location enabled. Don’t let a developer guilt-trip you into giving away your exact coordinates 24/7.
Auditing the Spy Network: Using the App Privacy Report
Even after disabling tracking, apps still communicate with external domains. The App Privacy Report is your secret weapon for auditing which third-party domains an app contacts, particularly when the app is idle (which is a major red flag).
Step-by-Step Guide: Reviewing Third-Party Contacts
- Go to Settings > Privacy & Security.
- Scroll down and tap App Privacy Report.
- Ensure the report is turned on. Review the data over the last seven days, focusing on the Network Activity section.
- Look for apps that contact suspicious or unknown domains, especially when you weren’t actively using them. For instance, if your note-taking app is contacting six different analytics domains, that’s a sign of a hidden SDK at work. If an app looks suspicious, the best move is to delete it entirely.
The Android Privacy Firewall (Active Management & Deletion)
Android’s approach to privacy requires a more proactive, hands-on role from the user, emphasizing active management and data deletion over relying on opt-out prompts. The key is to sever the link to your Advertising ID and meticulously monitor sensor usage.
The Essential Android Step: Deleting the Advertising ID
Resetting the Google Advertising ID (GAID) on Android only assigns a new ID but retains remnants of your old profile, allowing advertisers to reconnect to your previous data.
Deleting the GAID, available on Android 12 and above, completely removes the ID and prevents future access, offering stronger privacy protection.
Step-by-Step Guide: Deleting Your Google Advertising ID (GAID)
- Open the Settings app on your Android device.
- Navigate to Security & privacy (or just Privacy on some devices).
- Look for and tap on Privacy controls or Ads.
- Tap on Ads (or Advertising ID).
- You will see the option to “Delete advertising ID.”
- Tap “Delete advertising ID” again to confirm.
Pro Tip: The wording here is vital. Always choose “Delete” over “Reset” to ensure your old profile is completely orphaned.
Utilizing the Privacy Dashboard for Sensor Auditing
Android’s Privacy Dashboard provides an excellent, centralized timeline of when and which apps accessed sensitive sensors like the Camera, Microphone, and Location over the last 24 hours.
Step-by-Step Guide: Checking the Privacy Dashboard
- Open Settings > Security & privacy > Privacy.
- Tap on Privacy Dashboard.
- Review the timeline for Location, Camera, and Microphone usage. If you see an app accessing your microphone at 3:00 AM while you were sleeping, you have found a prime suspect for unauthorized activity.
- Tap on a permission (e.g., Microphone) to see a full list of apps that accessed it and review their permissions.
Granular Permissions and Auto-Reset
When granting new permissions on Android, always use the “Ask every time” or “While using the app” options.
Furthermore, Android has a feature that automatically revokes permissions from apps you haven’t used in a while. Make sure this is active.
Step-by-Step Guide: Enabling Permission Auto-Reset
- Open Settings > Apps > See all apps.
- Select an app.
- Scroll down to Unused app settings (or Permissions then Remove permissions if app is unused).
- Ensure the toggle for “Pause app activity if unused” or a similar feature is ON. This automatically revokes permissions like location and storage access for dormant apps, which is great for digital hygiene.
Advanced Defenses: External Shields Against Fingerprinting
No matter how well you configure your OS settings, the Tier 2 threat of Device Fingerprinting and hidden SDKs communicating with tracking domains remains. To combat this, we need to implement external shields that block these communications at the network level.
Blocking Trackers at the Source with Private DNS
The most advanced way to block known tracking domains (including those used by hidden third-party SDKs) is through Network Filtering via Custom DNS.
By directing all your network requests through a specialized DNS server that maintains a blocklist of known trackers, you stop the communication before it even leaves your phone.
Android Setup: Private DNS (The Easy Way)
Android 9 (Pie) and newer versions support DNS-over-TLS (DoT), which allows users to set a custom, encrypted DNS provider directly in the system settings.
This feature encrypts DNS queries, preventing third parties from spying on your DNS requests and enhancing your online privacy without needing root access or additional apps.
Step-by-Step Guide: Setting up Private DNS on Android 9+
- Open Settings >Network & internet (or Connections > More connection settings).
- Scroll down and tap Private DNS.
- Select the Private DNS provider hostname option.
- In the hostname field, enter a hostname from a reputable, ad-blocking DNS provider. For a robust tracking block, I recommend using a service like
dns.adguard.com(a service dedicated to blocking tracking and ads). - Tap Save. Your phone’s network traffic is now filtered and encrypted at the DNS level.
iOS Setup: Network Filtering (Requires an App)
Apple’s iOS does not offer a native system-wide Private DNS setting like Android. To achieve the same network-level blocking, you must use a third-party app that configures a local VPN profile or uses a DNS proxy feature (e.g., the Cloudflare 1.1.1.1 app or a similar ad-blocking utility).
- Download a reputable DNS/VPN app (e.g., Cloudflare WARP or AdGuard).
- Follow the app’s instructions to enable its filtering or DoT service. This will typically install a local VPN configuration profile that routes your traffic through the service’s encrypted, filtered DNS server.
Defeating Browser Fingerprinting with Privacy Browsers
Standard mobile browsers (Chrome, Safari, etc.) are highly susceptible to browser fingerprinting, which uses the unique combination of your browser, OS, installed fonts, and screen resolution to identify you. The solution is to switch to a dedicated Privacy Browser.
Expert Recommendation: I strongly recommend making a browser with built-in anti-fingerprinting technology your default for all general browsing.
- Brave Browser: Known for aggressive ad-blocking and sophisticated fingerprinting randomization technology.
- DuckDuckGo Privacy Browser: Focuses on blocking hidden trackers and forces sites to use an encrypted connection (HTTPS).
By using one of these browsers, you are actively countering the low-level data collection that happens simply by navigating the web, even if your network is already filtered by Private DNS.
The Complete Anti-Spying Strategy Checklist
To truly stop apps from spying on you, you need to execute a strategy that combines all three pillars we’ve discussed: Informed Consent, Granular Permission Reduction, and External Shields.
| Pillar | iPhone Action | Android Action |
| Informed Consent | Disable Global Tracking: Turn off “Allow Apps to Request to Track.” | Delete Advertising ID (GAID): Explicitly choose ‘Delete’ over ‘Reset’ GAID. |
| Granular Permission Reduction | Location & Sensors: Use “While Using the App” + Approximate Location. | Location & Sensors: Use “Just Once” or “While Using the App.” |
| Data Audit | App Privacy Report: Regularly review suspicious third-party domain contacts, especially when apps are idle. | Privacy Dashboard: Review the timeline for Camera, Mic, and Location access over the last 24 hours. |
| External Shields | Network Filtering: Use a third-party app/VPN for Private DNS (e.g., Cloudflare WARP). | Private DNS: Set provider hostname to a blocking service (e.g., dns.adguard.com). |
| Web Browsing | Switch to a privacy browser (e.g., Brave or DuckDuckGo). | Switch to a privacy browser (e.g., Brave or DuckDuckGo). |
Frequently Asked Questions (FAQs)
Q: Does a VPN stop apps from spying on me?
A: A Virtual Private Network (VPN) is an excellent first step because it encrypts your internet traffic and hides your IP address, which is a key component in a device fingerprint.
However, a VPN alone will not stop apps from spying on you because it does not address Tier 2 Permissionless Device Fingerprinting, which gathers data like your GPU rendering details or device clock skew.
Furthermore, a VPN fails to block third-party SDKs already embedded in the apps from communicating with their dedicated tracking domains.
The best defense is a VPN combined with the other steps listed in this guide.
Q: What is the risk of “Permissionless Device Fingerprinting” and how can I stop it?
A: Permissionless Device Fingerprinting is a major risk because it’s a permanent, high-accuracy device signature created by aggregating system properties (like GPU details and time settings) that does not require OS permission to collect.
You stop it by using External Shields—specifically, by enabling a Custom Private DNS to block communication with known fingerprinting servers at the network level, and by using privacy browsers that actively randomize or suppress the data points fingerprinting scripts try to read.
Q: Why is deleting my Google Advertising ID (GAID) better than resetting it on Android?
A: Deleting your GAID is significantly better than merely resetting it because deletion severs the link to your old advertising profile entirely. When you reset it, the old profile still exists, and some trackers might try to link the new ID back to the old one.
When you choose Delete, any app that subsequently attempts to read your GAID receives a string of zeros, effectively invalidating the identifier for tracking purposes and disrupting the Tier 1 tracking mechanism.
Q: Is it safe to grant location access as “While Using the App” for most apps?
A: Yes, in my professional opinion, it is generally safe and highly recommended to only grant location access as “While Using the App” for the vast majority of applications.
Apps only need your location at the moment they are running to provide a service. Granting “Always” access allows the app to collect and transmit your location data 24/7, which is an unnecessary privacy risk. Furthermore, on iPhone, always pair this with the Approximate Location setting.
Q: Are Free Apps more likely to spy on me than Paid Apps?
A: Based on my years of reviewing software, apps that are offered completely for free are significantly more likely to rely on aggressive tracking to monetize their user base.
This monetization often comes through embedding numerous third-party advertising, analytics, and social media SDKs, which are often the primary vehicles for hidden tracking and data collection.
Paid apps, having already monetized the user, generally have less financial incentive to engage in pervasive tracking, though they are not always tracker-free. I always recommend checking an app’s privacy label or permissions before downloading, regardless of the price.

